Operational technology (OT) systems are critical to modern industry. As these systems become more connected, cyberattacks present a significant risk, making strong OT threat detection and response tools essential.
Understand Your OT System
Start by mapping your industrial environment. Identify all connected assets, including sensors, HMIs, IoT devices and network segments. Document how these systems communicate, such as the protocols they use and their role in your overall operations. A complete picture helps you choose tools to monitor and protect your setup accurately.
Look for Potential Threats and Vulnerabilities
Next, analyze where the risks may come from. Common OT threats include malware, ransomware, insider attacks, unpatched legacy controllers and weak segmentation. Use real data from your actual network and past security incidents. You can also use specialized tools or hire a third party to assess you.
Identify Your Security Requirements
The right OT security tool depends on your environment’s unique operational demands. When defining what you need, consider the following categories:
- Regulatory compliance: Assess whether your sector requires adherence to specific security frameworks like NIST CSF or GDPR. Choose a tool that includes reporting and audit trails that help you stay compliant without a significant added workload.
- Industry best practices: Aside from legal guidelines and regulatory frameworks, consider best practices specific to your industry. Work with your peers and gather relevant insights from online communities, meetings or networking events.
- Scalability and flexibility: Your OT environment will evolve, so your security solution must support diverse vendor equipment, legacy systems or multiple location needs. Flexible architecture ensures the system remains effective as your operations expand.
Evaluate Different OT Cybersecurity Solutions
Once you have identified your unique OT environment and security requirements, explore your prospects, evaluating them on essential criteria and functionality:
- Comprehensive asset visibility: Effective tools must identify and classify assets, communication workflows, firmware versions and protocols used. Asset visibility is essential for precise monitoring and incident response.
- Advanced threat detection capabilities: Look for solutions with anomaly detection, extensive threat intelligence and automated defenses. AI-powered detection is especially powerful, even for new systems that lack extensive historical data. These features allow you to address incoming threats before they escalate.
- Vulnerability management and risk prioritization: Tools should highlight vulnerabilities based on severity and operational relevance. Prioritizing high-impact risks is critical to ensure operational continuity.
- Incident response: Check whether the platform offers automated containment, response workflows or guided investigations, as well as its availability. Strong response capabilities allow you to act quickly and maximize uptime.
- Integration capabilities: Your OT security tool should work seamlessly with your existing workflows and devices. Smooth integration ensures adequate protection and more cost-effective implementation.
Assess Each Provider
Aside from evaluating the platform’s features, make sure to assess the provider, as well. Choose vendors with deep experience in OT or critical infrastructure. Specialized entities are more capable of addressing unique protocol requirements and operational risks.
Check case studies, feedback and peer reviews to evaluate their reputation. These sources can help you understand how the tool performs in real-world scenarios, as well as the vendor’s responsiveness and customer service quality.
Ask for a Trial Period
Ask prospective vendors for a trial period or proof-of-concept deployment to see how the tool behaves in your specific environment. This stage can reveal its responsiveness, usability and integration.
What Are the Best Tools for OT Threat Detection and Response?
If you’re looking for an OT threat detection and response tool for your enterprise, consider these top options.
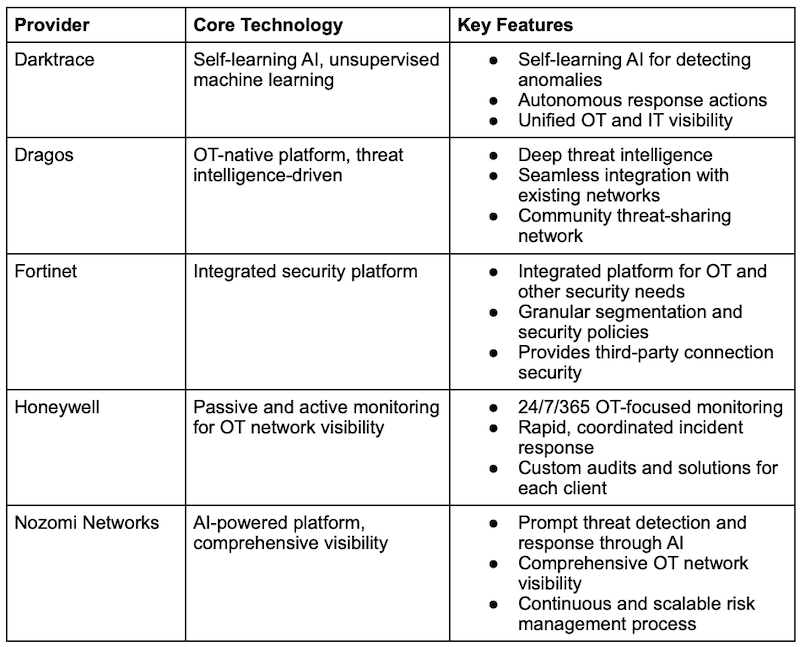
1. Darktrace
Darktrace brings an AI-driven approach to OT cybersecurity. Its self-learning agent combines multiple models to discover unique baselines or patterns for every asset in your environment. It can then detect when something deviates from normal behavior, giving operators real-time and accurate visibility.
Key Features
- Self-learning AI for detecting anomalies
- Autonomous response actions
- Unified OT and IT visibility
2. Dragos
Dragos is well-known in the OT cybersecurity industry for its asset identification, network mapping and effective incident response workflows. It detects malicious activity by combining behavioral analytics with extensive industrial threat intelligence.
Key Features
- Deep threat intelligence
- Seamless integration with existing networks
- Community threat-sharing network
3. Fortinet
Fortinet’s OT security solution extends the company’s well-known network security platform into industrial environments. It effectively combines asset discovery with precise segmentation and secure connections, allowing users to protect even legacy networks and devices effectively.
Key Features
- Integrated platform for OT and other security needs
- Granular segmentation and security policies
- Provides third-party connection security
4. Honeywell
Honeywell is an established cybersecurity provider with extensive experience in industrial settings. Its OT security solutions prioritize compliance, risk reduction and resilience through 24/7 monitoring and rapid response.
Key Features
- 24/7/365 OT-focused monitoring
- Rapid, coordinated incident response
- Custom audits and solutions for each client
5. Nozomi Networks
Nozomi Networks provides OT visibility and threat detection using passive network monitoring and AI-powered analysis. It identifies assets, maps communications and alerts operators to anomalies or known threat patterns.
Key Features
- Prompt threat detection and response through AI
- Comprehensive OT network visibility
- Continuous and scalable risk management process
OT Threat Detection and Response Tools at a Glance
Strengthening OT Cybersecurity
Choosing the right OT threat detection and response tool requires understanding your environment, identifying your risks and selecting a platform that delivers on your requirements. Investing in a dedicated OT cybersecurity solution is crucial for protecting critical processes and responding to threats promptly.